Issue Definition:
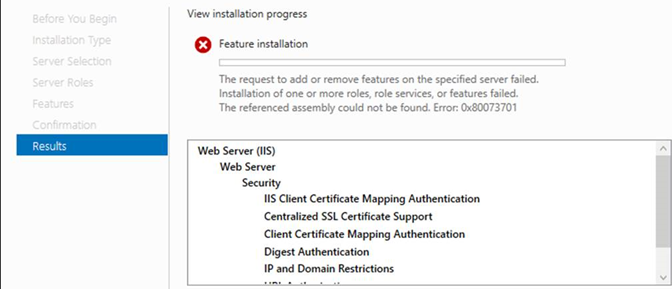
Failed to install IIS, Failover Cluster roles on one Windows Server 2019 named with error 0x80073701.
Scope Agreement:
We consider the case as resolved when this issue has been fixed, or the root cause is identified to be product by-design issue, or a third-party issue, which is not supported by Microsoft, we will also let you know.
We are now working together to resolve your issue. If you do not agree with the scope defined above, or would like to amend it, please let me know as soon as possible.
Analysis:
Refer log below-:
C:\Windows\Logs\CBS CBS.log to analyze which KB is creating issue.
1. From the output of running restorehealth, we noticed that there’s some corruptions related to patch KB5014669 and KB5014022.
2023-05-09 09:26:34, Info CBS =================================
2023-05-09 09:26:34, Info CBS Checking System Update Readiness.
2023-05-09 09:26:34, Info CBS
2023-05-09 09:26:34, Info CBS (p) CBS Catalog Missing (n) Package_5472_for_KB5014669~31bf3856ad364e35~amd64~~10.0.1.10
2023-05-09 09:26:34, Info CBS Repair failed: Missing replacement mum/cat pair.
2023-05-09 09:26:34, Info CBS (p) CBS Catalog Missing (n) Package_5477_for_KB5014669~31bf3856ad364e35~amd64~~10.0.1.10
2023-05-09 09:26:34, Info CBS Repair failed: Missing replacement mum/cat pair.
2023-05-09 09:26:34, Info CBS (p) CBS Catalog Missing (n) Package_5480_for_KB5014669~31bf3856ad364e35~amd64~~10.0.1.10
2023-05-09 09:26:34, Info CBS Repair failed: Missing replacement mum/cat pair.
2023-05-09 09:26:34, Info CBS (p) CBS Catalog Missing (n) Package_5483_for_KB5014669~31bf3856ad364e35~amd64~~10.0.1.10
2023-05-09 09:26:34, Info CBS Repair failed: Missing replacement mum/cat pair.
2023-05-09 09:26:34, Info CBS (p) CBS Catalog Missing (n) Package_5487_for_KB5014669~31bf3856ad364e35~amd64~~10.0.1.10
2023-05-09 09:26:34, Info CBS Repair failed: Missing replacement mum/cat pair.
…
2023-05-09 09:26:34, Info CBS (w) CBS Package Index Package Missing 0x80070490 Package_2566_for_KB5014022~31bf3856ad364e35~amd64~~0.0.0.0 Package_2566_for_KB5014022~31bf3856ad364e35~amd64~~10.0.1.14
2023-05-09 09:26:34, Info CBS (w) CBS Package Index Package Missing 0x80070490 Package_2567_for_KB5014022~31bf3856ad364e35~amd64~~0.0.0.0 Package_2567_for_KB5014022~31bf3856ad364e35~amd64~~10.0.1.14
2023-05-09 09:26:34, Info CBS (w) CBS Package Index Package Missing 0x80070490 Package_2572_for_KB5014022~31bf3856ad364e35~amd64~~0.0.0.0 Package_2572_for_KB5014022~31bf3856ad364e35~amd64~~10.0.1.14
2023-05-09 09:26:34, Info CBS (w) CBS Package Index Package Missing 0x80070490 Package_2577_for_KB5014022~31bf3856ad364e35~amd64~~0.0.0.0 Package_2577_for_KB5014022~31bf3856ad364e35~amd64~~10.0.1.14
2023-05-09 09:26:34, Info CBS (w) CBS Package Index Package Missing 0x80070490 Package_2578_for_KB5014022~31bf3856ad364e35~amd64~~0.0.0.0 Package_2578_for_KB5014022~31bf3856ad364e35~amd64~~10.0.1.14
…
2023-05-09 09:32:04, Info CBS Summary:
2023-05-09 09:32:04, Info CBS Operation: Detect and Repair
2023-05-09 09:32:04, Info CBS Operation result: 0x800f0954
2023-05-09 09:32:04, Info CBS Last Successful Step: Entire operation completes.
2023-05-09 09:32:04, Info CBS Total Detected Corruption: 28026
2023-05-09 09:32:04, Info CBS CBS Manifest Corruption: 19
2023-05-09 09:32:04, Info CBS CBS Metadata Corruption: 28005
2023-05-09 09:32:04, Info CBS CSI Manifest Corruption: 0
2023-05-09 09:32:04, Info CBS CSI Metadata Corruption: 0
2023-05-09 09:32:04, Info CBS CSI Payload Corruption: 2
2023-05-09 09:32:04, Info CBS Total Repaired Corruption: 0
2023-05-09 09:32:05, Info CBS CBS Manifest Repaired: 0
2023-05-09 09:32:05, Info CBS CSI Manifest Repaired: 0
2023-05-09 09:32:05, Info CBS CSI Payload Repaired: 0
2023-05-09 09:32:05, Info CBS CSI Store Metadata refreshed: True
2. From CBS log, we noticed that the IIS roles failed to be installed with error 0x80073701 due to KB5014669 corruption.
2023-05-09 09:34:05, Error CSI 000068ef (F) STATUS_SXS_ASSEMBLY_MISSING #56773556# from CCSDirectTransaction::OperateEnding at index 0 of 1 operations, disposition 2[gle=0xd015000c]
2023-05-09 09:34:05, Error CSI 000068f0 (F) HRESULT_FROM_WIN32(ERROR_SXS_ASSEMBLY_MISSING) #56773398# from Windows::ServicingAPI::CCSITransaction::ICSITransaction_PinDeployment(Flags = 0, a = be61d6ca2ab4dcc4eede90c05a096ade, version 10.0.17763.1790, arch amd64, nonSxS, pkt {l:8 b:31bf3856ad364e35}, cb = (null), s = (null), rid = 'Package_5931_for_KB5014669~31bf3856ad364e35~amd64~~10.0.1.10.5014669-10806_neutral', rah = (null), manpath = (null), catpath = (null), ed = 0, disp = 0)[gle=0x80073701]
2023-05-09 09:34:05, Info CBS Failed to pin deployment while resolving Update: Package_5931_for_KB5014669~31bf3856ad364e35~amd64~~10.0.1.10.5014669-10806_neutral from file: (null) [HRESULT = 0x80073701 - ERROR_SXS_ASSEMBLY_MISSING]
2023-05-09 09:34:05, Info CBS Failed to bulk stage deployment manifest and pin deployment for package:Package_3995_for_KB5023702~31bf3856ad364e35~amd64~~10.0.1.10 [HRESULT = 0x80073701 - ERROR_SXS_ASSEMBLY_MISSING]
2023-05-09 09:34:05, Info CBS CommitPackagesState: Started persisting state of packages
2023-05-09 09:34:05, Info CBS CommitPackagesState: Completed persisting state of packages
2023-05-09 09:34:05, Info CSI 000068f1@2023/5/9:02:34:05.375 CSI Transaction @0x1bde6e79700 destroyed
2023-05-09 09:34:05, Info CBS Perf: Resolve chain complete.
2023-05-09 09:34:05, Info CBS Failed to resolve execution chain. [HRESULT = 0x80073701 - ERROR_SXS_ASSEMBLY_MISSING]
2023-05-09 09:34:05, Error CBS Failed to process single phase execution. [HRESULT = 0x80073701 - ERROR_SXS_ASSEMBLY_MISSING]
2023-05-09 09:34:05, Info CBS WER: Generating failure report for package: Microsoft-Windows-Foundation-Package~31bf3856ad364e35~amd64~~10.0.17763.1, status: 0x80073701, failure source: Resolve, start state: Installed, target state: Installed, client id: DISM Package Manager Provider
Next Action:
I noticed that you told that have tried the workaround provided in case #2303240010000356, which I believe is running remove-Item -path "HKLM:\SOFTWARE\Microsoft\Windows\CurrentVersion\Component Based Servicing\Packages\*KB5014022*" with PowerShell. (If I misunderstood, please let me know.) Please help confirm if you have backup for the Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Component Based Servicing\Packages key before you running the script?
If so,
1. Please restore the backup
2. Run below script to remove the registry key for KB5014669 with PowerShell.
remove-Item -path "HKLM:\SOFTWARE\Microsoft\Windows\CurrentVersion\Component Based Servicing\Packages\*KB5014669*"
3. Please reinstall the IIS roles and check if it could be installed then.
If no backup prepared,
1. Please backup the reg key Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Component Based Servicing\Packages
2. Run below script to remove the registry key for KB5014669 with PowerShell.
remove-Item -path "HKLM:\SOFTWARE\Microsoft\Windows\CurrentVersion\Component Based Servicing\Packages\*KB5014669*"
3. Reinstall the package KB5014022 with instructions below as well.
- Create folder C:\Temp\cab
- Download patch from Microsoft Update Catalog by searching the KB number and save under C:\Temp.
- Run the following script with cmd as administrator to extract the installer
Expand -f:* <File Path> C:\Temp\cab
(For example: Expand -f:* C:\Temp\Windows10.0-KB5008212.msu C:\Temp\cab)
- You will see CAB file created under C:\Temp\cab, please run below script to remove the package,
Dism /online /remove-package /packagepath:<cab file path>
(For example: dism /online /remove-package /packagepath:C:\Temp\Windows10.0-KB5008212-x64.cab )
- Then run below script to reinstall it.
Dism /online /add-package /packagepath:<cab file path>
(For example: dism /online /add-package /packagepath:C:\Temp\Windows10.0-KB5008212-x64.cab )
4. Please reinstall the IIS roles and check if it could be installed then.